Apply Unis Comprehensive Protection of Every Trust
Data security is the lifeline of Apply Unis. We prioritize the security of customer data as our top priority.
Protecting customer data security is the fundamental principle of Apply Unis and the cornerstone of mutual trust between Apply Unis and customers.
Protecting customer data security is the fundamental principle of Apply Unis and the cornerstone of mutual trust between Apply Unis and customers.
Cooperation begins with trust, and security is paramount above all else.
Your data will not be lost
Our supporting data centers are located in Shanghai and Hangzhou respectively. The business databases are regularly snapshot and backed up, with data storage using a dual-site triple-backup approach, implementing a dual-data double-insurance mechanism: primary storage is on Alibaba Cloud, with backups on Huawei Cloud. Additionally, we have a backup execution monitoring mechanism to ensure the integrity of data backups, and regular backup data recovery tests are conducted.
Your data is exclusively accessible to you
Apply Unis will allocate unique security keys to each customer, who can also choose a self-managed key scheme. These keys are used to encrypt customer data, ensuring that data is encrypted before storage. Not only is customer data isolated from each other, but Apply Unis internally cannot access customer data. If you require our assistance in configuring your system, authorization from you is needed to add authorized accounts to your system.
Your data security is guaranteed
Apply Unis has implemented stringent security protection and management solutions at every stage of data collection, transmission, and storage, covering various encryption measures and full-process monitoring. Any anomalies are detected and addressed promptly to ensure data security throughout its lifecycle. Core sensitive data is encrypted using the AES advanced encryption algorithm, and confidentiality agreements are signed with each institutional client.
Apply Unis Security and Compliance System
By constructing a comprehensive security defense system and integrating top-notch security services and operations, security becomes a natural attribute of Apply Unis. The powerful and comprehensive security and compliance system is built through product solutions and service capabilities in the three major modules of security, compliance, and privacy. This system assists enterprise security administrators in implementing corporate security management systems and helps customers meet dynamically changing data compliance requirements.
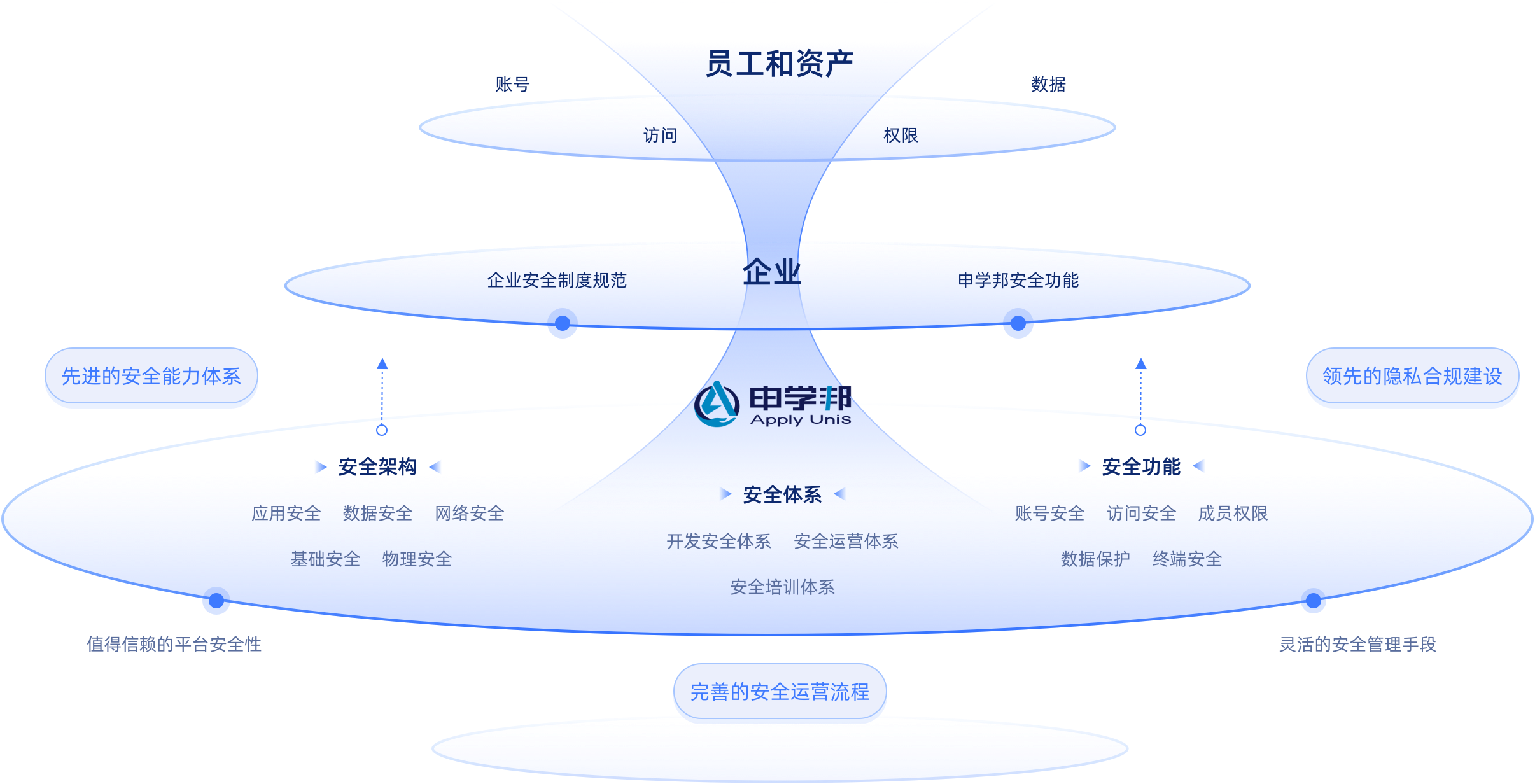
Several Major Security Measures to Fully Protect Your Data Securit
Powerful Product Security Features | Reliable Fundamental Security Architecture | Efficient and Reliable Security Development and Operations System

Account Security
We support seamless integration through standard protocols and our existing enterprise identity platforms to achieve Single Sign-On (SSO), maintaining our existing account security standards and policies within the enterprise. We also support direct authentication, two-step verification, and other functions to enhance account security.

Physical Security
We adopt high-level physical security standards to build our exclusive data center for Apply Unis, which features powerful and stable performance.

Security Development Lifecycle Management
We establish a comprehensive SDLC (Software Development Lifecycle) management process, with security and compliance assessments and automated risk discovery at each stage. Combined with red team-blue team testing in our cyber warfare laboratory, we ensure closed-loop issue resolution to protect user data privacy.

Member Permissions
We provide flexible means of permission control to help administrators grant organization members the least necessary permissions, avoiding information leaks caused by improper permission configurations and enhancing enterprise security levels.

Basic Security
Through baseline detection, vulnerability scanning, intrusion detection, container security, service isolation, and zero-trust access mechanisms, we ensure the 24/7 secure operation of Apply Unis' business.

Vulnerability Operations
Through a vulnerability management process, we promptly and comprehensively discover and follow up on vulnerabilities to ensure the confidentiality, security, and availability of the Apply Unis' system resources. We establish a complete threat intelligence system to promptly perceive the existence of external threats, ensuring that the default built-in security capabilities remain at a high level.

Data Protection
For core data transmission scenarios, it offers data leakage prevention capabilities. To address the risk of screen capture leaks, it provides screen watermarking. This assists enterprises in better managing information security risks.

Network Security
Based on Alibaba Cloud and Huawei Cloud network equipment clusters, independently networked and isolated from each other, multi-active deployment with device-level disaster recovery, equipped with powerful gateways and access control mechanisms, encrypting communication transmissions, combined with cloud security to defend against external intrusions and hijacking.

Standard Development and Deployment Process
Apply Unis adopts an internet standard development and deployment process, which includes three environments: intranet, pre-production, and production. Functionality development and deployment are required to pass acceptance tests in the intranet and pre-production environments sequentially before going live.

Access Security
By adhering to the zero-trust principle of "always verify," we continuously verify users' access requests based on factors such as identity, network, and device. Organizations can restrict members to access enterprise resources only in specific environments, effectively reducing the risk of information leakage.

Data Security
We have comprehensive control over the data lifecycle, with clear processes and technological safeguards in place for data creation, storage, transmission, access, and disposal. We provide flexible key management solutions to ensure the security of user data.

Emergency Response
Apply Unis has established an emergency response team and formulated standard emergency response procedures for all security incidents. Based on alerts, feedback, intelligence, and other clues, all security incidents are pre-judged, and response and disposal work is carried out for the first time to ensure the normal and continuous operation of user business.

Endpoint Security
Considering the rapid increase in demands such as mobile office and BYOD, Apply Unis provides lightweight endpoint management capabilities, including mobile file encryption and paste protection, to ensure that Ally Unis' internal assets cannot be transferred to user endpoints.

Application Security
Security capabilities such as identity recognition and permission control systems, combined with powerful cloud security technologies, ensure the operational and production security of the Appl Unis' client and server.

Flexible Deployment Modes
The Apply Unis' project supports both public cloud SAAS rental and independent deployment requirements for medium and large institutions, fully meeting the needs of different types of organizations.
Our Trusted Commitment
@2x.png)
You control the data
You can verify its confidentiality and integrity at any time, whether it is in storage, processing, or transmission.
@2x.png)
Strong integrated security
We ensure the security of the cloud platform itself and provide security capabilities to cloud users, assisting in building a comprehensive security environment.
备份@2x.png)
Continuous output of security practices across the industry
Utilizing our experience serving millions of users, we pass on best practices of high trustworthiness to all users.
@2x.png)
Collaboratively trace event impacts
Verify cloud security and compliance, and work with customers to track and resolve operations that may cause issues.
@2x.png)
Customer needs are top priority
We will work closely with customers and regulatory agencies, treating user security, privacy, and compliance as vital.

Apply Unis
has obtained ISO 27001 Information Security Management System certification
ISO 27001 is the most widely recognized information security management standard, and organizations adhere to this standard to safeguard data assets. Implementing ISO 27001 reflects our organization's commitment at all levels to maintaining the security of user information.
The internal security policy of Apply Unis is governed by ISO 27001 and includes the following key points:
- All access to production data is strictly controlled and restricted.
- Monitoring and controlling physical access to laptops and servers.
- Maintaining high security for passwords.
- Scanning all devices accessing our systems for malware and centralized management.
- All users undergo necessary security training annually.
- Our security incident response team is on standby 24/7, conducting regular weekly meetings to review security status.
- We remain vigilant against new security threats, monitoring reported major violations and vulnerabilities to understand their potential impact on operations.




















